insights
How to Exploit SSH to distribute Malware
by Giorgio Romeo – 04 Jun 2025

An analysis shows that malicious files, such as compressed Python files, can be executed without warnings on the desktop version of WhatsApp, representing a serious vulnerability.
29 May 2025
A list of the top 10 Open Source Intelligence (OSINT) tools for cybersecurity. Let’s explore the essential tools for collecting and analyzing OSINT data in intelligence activities, aimed at understanding and addressing cyber threats and attacks.
28 May 2025
Passwordless authentication allows users to access systems without using passwords or PINs, relying instead on biometric factors or physical devices, offering enhanced security and reduced management costs.
27 May 2025
If you want to reclaim your digital space in a world where “free” means being the product, Mastodon is one of the few platforms that aligns with the principles of privacy, transparency, and freedom.
26 May 2025
Some online claims have raised concerns about a supposed feature, expected in June 2025, that would allow automatic synchronization between personal and business accounts. Let's clarify.
25 May 2025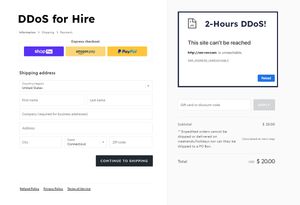
DDoS attacks are on the rise thanks to DDoS-for-hire services available on the dark web and Telegram. These attacks use botnets to overwhelm services and can target any device connected to the internet. Launching a DDoS attack has become accessible to anyone—and for just a few dollars.
14 Apr 2025
Our selection of the best 5 OSINT sources that provide valuable data for analysts and blue teamers to strengthen defenses and monitor ongoing phishing attacks.
31 Mar 2025
In the world of cybersecurity, malware analysis is a critical challenge to ensure the security of networks and computer systems. This article presents five often-overlooked but essential tools for analysts and cybersecurity professionals.
20 Jan 2025
Volatility in Digital Forensics: how to use the framework to analyze memory dumps from Windows systems, perform forensic RAM analysis, and examine active connections, running processes, registry keys, and more.
13 Jan 2025