In the vast and ever-changing world of cybersecurity, one of the most pressing challenges experts face is malware analysis.
Malware, or malicious software, represents a constant threat to individuals, businesses, and institutions around the world. Understanding how they work and how to counter them is crucial to maintaining the security of networks and computer systems. But where does malware analysis begin, and how can we approach it successfully?
In this article, we will explore the field of malware analysis by presenting five underrated tools that every aspiring analyst or cybersecurity professional should learn to master. These tools are great assets for understanding the complexity of malware, identifying their evasive techniques, and developing effective countermeasures. But before diving into the specifics of the technologies, it's essential to understand the context in which malware analysts operate; for this purpose, we’ve linked at the end of the article a guide on how to create a malware analysis environment from scratch.
Let’s now dive into the presentation of these five excellent tools we recommend exploring and learning:
- PeStudio
- DnSpy
- Detect it Easy (DiE)
- Ghidra
- Process Hacker
PeStudio
PeStudio is a widely used malware and Windows application analysis tool in the field of cybersecurity. This software allows for the extraction of many characteristics of Windows executable files.
With PeStudio, it is possible to statically examine files, providing detailed information about metadata, dynamic libraries, digital certificates, and more. This static analysis helps quickly identify any indicators of compromise (IoC) present within malware.
In fact, the software can automatically detect what might be considered IoCs within the examined files, assisting analysts in identifying potential threats or suspicious behavior.
For example, by looking at the imported libraries of a sample, we can easily guess if it behaves maliciously. In this, PeStudio helps by flagging libraries that are frequently abused by malware. Another very useful resource in this context is the website Malapi.io, an updated repository by researchers that lists malware abusing Windows APIs for malicious purposes.
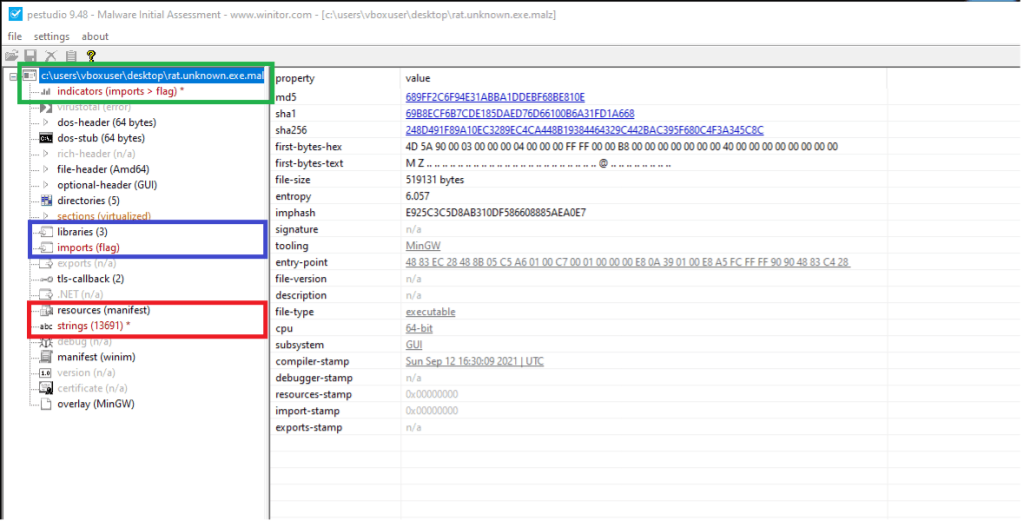
The visualization of imported libraries is not the only feature of PeStudio; with this software, it is also possible to extract and analyze strings and resources within files, revealing valuable information about the application's behavior and functionality.
DnSpy
DnSpy is an indispensable open-source tool for developers and malware analysts working with .NET applications. It offers full access to source code, making it easier to analyze, modify, and understand .NET applications in detail.
DnSpy allows for the easy decompilation of .NET assemblies, enabling developers to examine the original source code of the .NET sample. It’s as simple as opening a .NET sample in DnSpy to gain full access to the fully decompiled source code.
DnSpy does not stop at decompiling code—it also integrates a debugger that allows step-by-step code execution, simplifying the process of identifying and understanding the behavior of a sample, particularly if it is obfuscated. Analysts can also modify the source code during the application’s execution, allowing for functionality testing or real-time behavioral analysis.
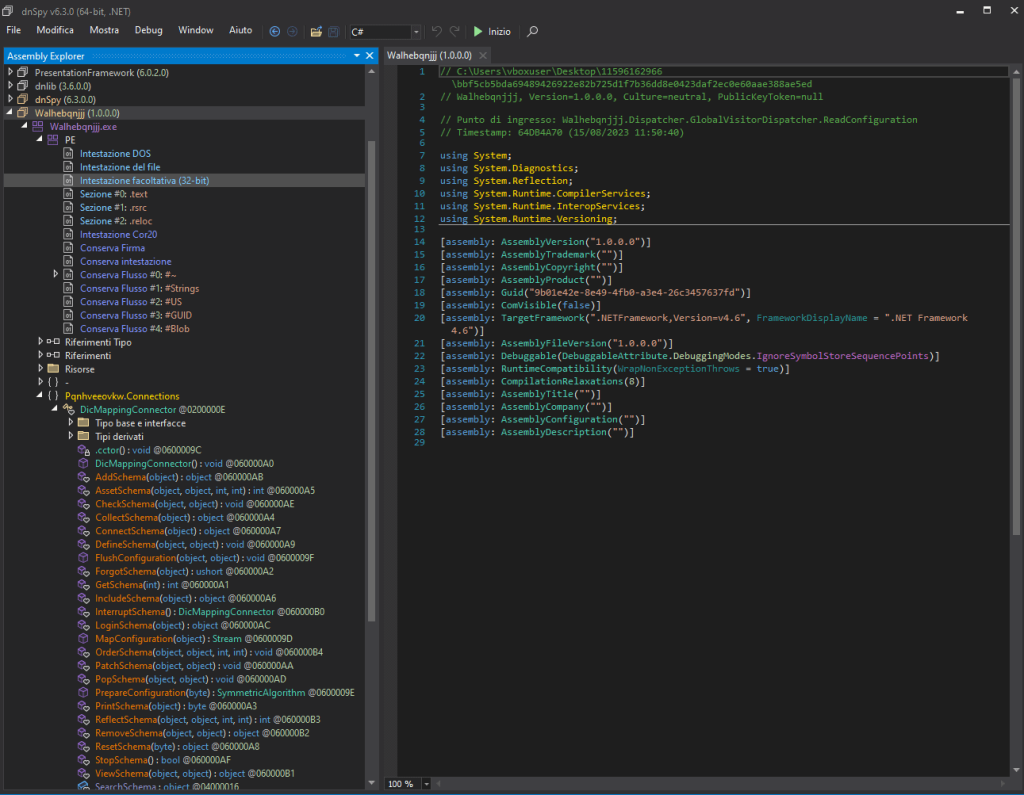
In the image above, we see how a sample looks when decompiled using this software. Under the PE section, the blue text represents various sections and resources of the sample; the yellow text shows the different classes, and the orange shows various methods within the selected class. Finally, in the right window, we see information about the file’s signature, if present, and at the top in green text, we have a shortcut to jump to the entry point and begin our debugging analysis.
Detect It Easy (DIE)
Detect It Easy (DIE) is an executable file analysis tool designed to simplify the identification and understanding of exe file nature. This open-source software is widely used by security analysts and reverse engineering enthusiasts to understand executable file structures, identify digital signatures, and detect potential IoCs.
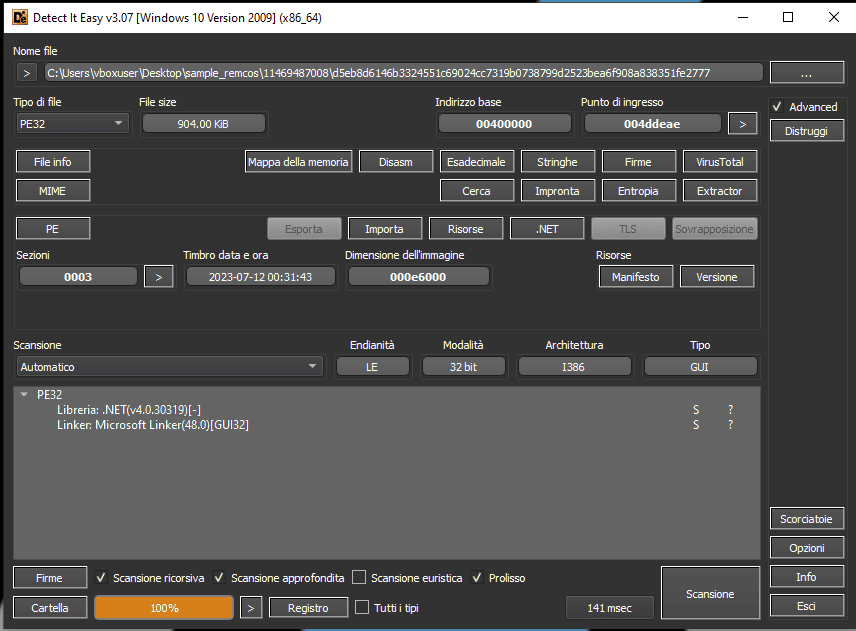
With this tool, it’s possible to automatically identify the format of the samples under analysis and the programming language they were written in.
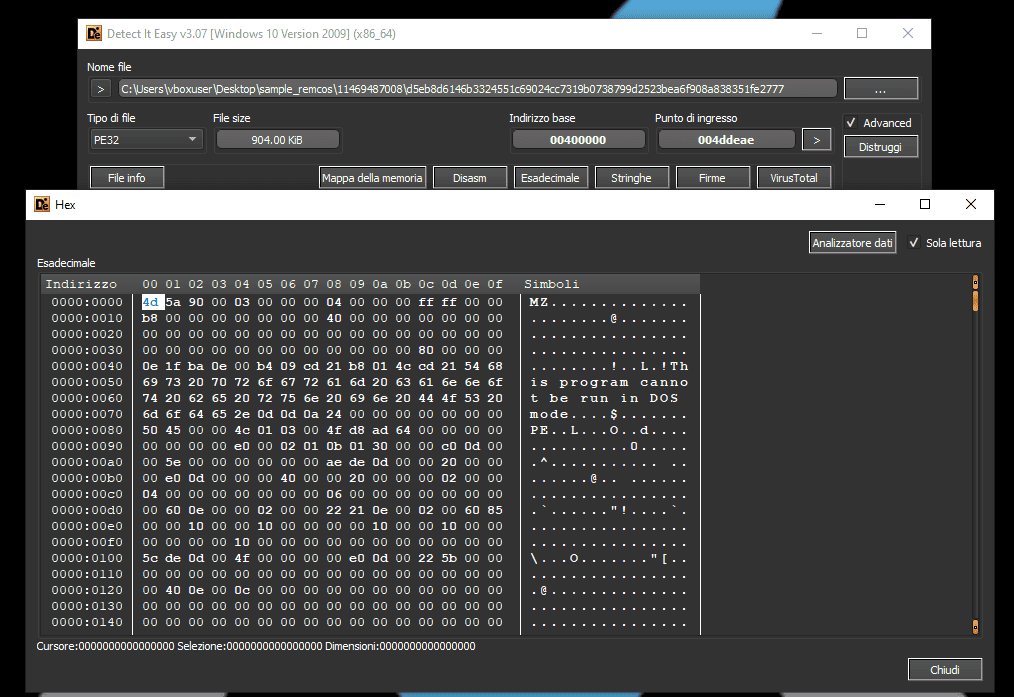
The software also allows users to view the resources a sample uses, display its hex (as shown above), and analyze different sections of the file. Finally, DIE includes a signature scanning feature, identifying files signed with unauthenticated digital signatures, making it easier to detect potential cyber threats.
Ghidra
Now we mention a very valid alternative to IDA Pro, a much better-known (and more expensive) reverse engineering software; Ghidra is a powerful open-source reverse engineering tool developed by the United States National Security Agency (NSA). It is widely used by security experts to analyze binary software code.
One of its most powerful features is its integrated decompiler. This tool can convert binary code (or machine language) into high-level source code (e.g., C/C++), allowing analysts to more easily understand software functionality.
The tool also provides a visualization of program flows, allowing users to follow the software’s execution path. This function is essential for understanding how the program responds to different situations and inputs. Ghidra can work with a wide range of binary file formats, including executables, dynamic libraries, firmware files, and more.
To begin our analysis, the binary code to be analyzed must be imported into Ghidra. This can be done by creating a new project and importing the binary file.
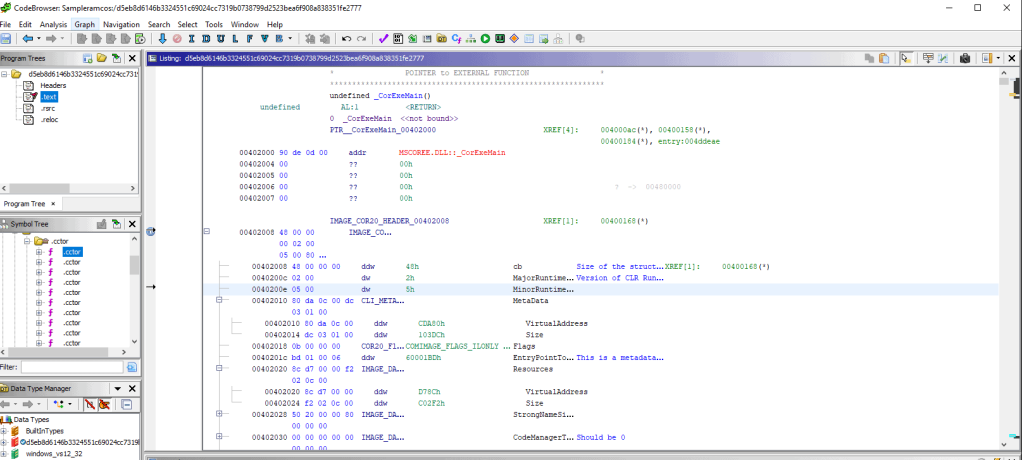
Once the file is imported, Ghidra begins automatic analysis. During this process, it identifies functions, variables, and other structures within the binary code. Users can then explore the decompiled source code, add comments, identify critical functions, and discover vulnerabilities or suspicious behaviors.
Process Hacker (in tandem with SysInternals' ProcMon)
Process Hacker is an open-source software designed for advanced monitoring and control of processes running on a Windows system. This tool offers a detailed view of running processes, system resources used, and network connections, allowing users to more effectively analyze and manage OS activity. Process Hacker is a powerful alternative to Windows Task Manager, with advanced and customizable features.
The tool provides a complete overview of running processes, including system processes, user applications, and services. Users can view detailed information such as PID (Process ID), CPU and memory usage, process owner, and more.
Analysts can search and filter processes based on various criteria, simplifying the search for specific processes or viewing processes with certain characteristics.
Process Hacker is extremely useful for malware analysts, especially for identifying suspicious or unwanted processes during dynamic analysis.
Although the tool already provides a solid view of a malware’s behavior, combining it with ProcMon, from the SysInternals suite, provides 360-degree control over the behavior of a suspicious file.
In fact, while Process Hacker offers detailed insight into processes, services, and system resources, ProcMon provides a detailed overview of activities, including system logs and process interactions with files and the network. Used together, Process Hacker provides specific process details, while ProcMon records the sample’s activity, allowing analysts to track and analyze in real time the malware’s behavior through processes, system key and registry modifications, files, network calls, and the creation of scheduled tasks or services, thereby enabling the detection of suspicious behavior.
Conclusions
With Process Hacker, we conclude this mini-guide on five tools that we believe are highly underrated considering the potential they offer. If you want to practice with these tools and need a secure environment to avoid risking your own resources, we recommend checking out our guide on how to create a malware analysis environment.