We increasingly hear about “hacker attacks on websites,” capable of causing disruptions and rendering affected sites inaccessible for hours.
Whether they are Ministry portals, airport websites, banks, or even giants like X (formerly Twitter), no one seems immune. But what exactly are these attacks? What is the real risk?
In the world of cybersecurity, this type of attack is called a DDoS (Distributed Denial of Service) and it’s not new—on the contrary, it has been used since the early days of the internet. In addition to conducting defacement activities—often with no real purpose—cybercriminals have realized that this could be a source of profit. In recent years, DDoS attacks offered as a service, also known as “DDoS-for-hire”, have increasingly become a reality.
These services allow anyone, even without technical skills, to launch cyberattacks against websites, servers, and digital infrastructures. The phenomenon is growing, fueled by the easy access to these offerings on the dark web and platforms as accessible as Telegram.
What Is a DDoS Attack and Its Different Types
A DDoS attack targets websites and servers by disrupting network services in an attempt to exhaust an application’s resources. The attackers send an enormous amount of traffic to the website, causing functionality issues or taking it entirely offline.
During a DDoS attack, a series of bots—or a botnet—sends a high volume of HTTP requests and traffic to a website or service. Essentially, multiple computers storm a single machine, pushing out legitimate users. As a result, the service may slow down or go offline for a period of time.
Denial of Service attacks can last hours or even days and can be directed at any publicly accessible device on the internet. They are sometimes used as a diversion while a more sophisticated attack is carried out on a server or database to access sensitive information.
There are several types of DDoS attacks, typically categorized into three main types: volumetric attacks, protocol attacks, and application-layer attacks.
HTTP Floods and Layer 7 Attacks
- Use HTTP flood attacks, sending millions of simultaneous web requests to target servers, consuming resources and rendering sites inaccessible.
- Target the application layer (Layer 7), which is the most difficult to mitigate because it mimics legitimate traffic.
SYN Flood and UDP Flood Attacks
- SYN Flood: Send a large number of incomplete connection requests, consuming server resources.
- UDP Flood: Generate massive volumes of UDP packets, saturating network bandwidth.
Carpet Bombing DDoS
- Distribute the attack across multiple IP addresses in an entire network rather than focusing on a single server, making it harder to block.
Botnet Amplification
- Use botnets made up of infected PCs, compromised servers, and IoT devices to generate large-scale traffic.
Some techniques also involve amplification attacks (e.g., DNS amplification, NTP reflection), which multiply the traffic sent to targets.
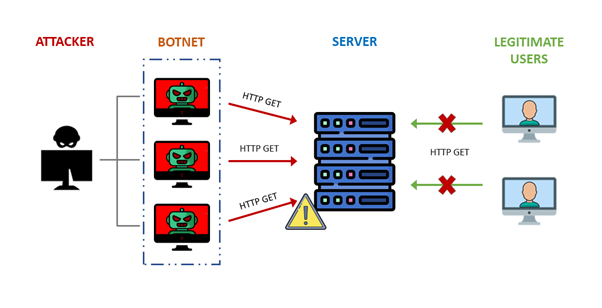
The DDoS-for-Hire Service Market
DDoS-for-hire services, often referred to as “booters” or “stressers”, are platforms that offer the ability to launch DDoS attacks for a fee. These attacks aim to overwhelm a target system with massive amounts of traffic, rendering it inaccessible to legitimate users. According to an analysis by Kaspersky, attackers can purchase ready-to-use solutions starting at $99.
In addition to purchasing, botnets can be rented or acquired as leaked source code at symbolic prices. In some cases, customized botnet development is also available. Prices vary depending on the power and duration of the attack, with costs reaching several thousand dollars for more sophisticated operations.
A botnet is a network of devices infected with malware, controlled by a malicious actor. These can include computers, servers, routers, and even IoT devices like security cameras and printers. A well-known example is Mirai, a botnet that scans the internet for IoT devices with weak passwords, infects them, and uses them to launch DDoS attacks.
Once created, botnets can be used for various purposes, including illegal cryptocurrency mining, malware distribution, and of course, DDoS attacks—launching large-scale offensives using the combined power of thousands of devices.
Buying a DDoS Attack on Telegram
Telegram, known for its end-to-end encryption and the ability to create public and private channels, has become fertile ground for all kinds of activity—including criminal ones. Within it, you can easily find channels and groups dedicated to services like DDoS attacks, stolen data sales, and phishing tools.
By doing a little research among criminal groups on Telegram, it doesn’t take long to come across such services:
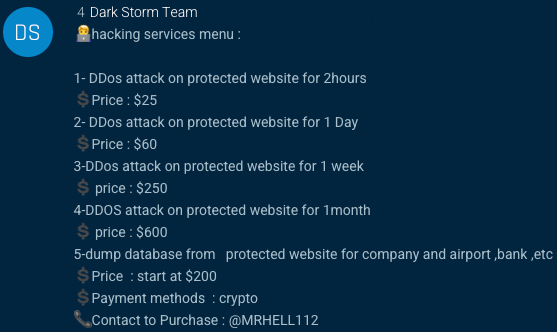
One of the most well-known groups in this context is the Dark Storm Team, which recently gained notoriety for allegedly taking Elon Musk’s social media platform (X) offline for several hours.
What’s truly shocking, however, is the cost: for a ridiculously low amount, accessible to virtually anyone, it’s possible to launch an attack against almost any target.
Operation PowerOFF
The good news is that the lifespan of these Telegram channels is getting shorter and shorter. It’s clear that the arrest of Pavel Durov (founder of Telegram) in France on August 24, 2024, has impacted the platform’s policies: thanks to greater cooperation with authorities, taking action against these channels has become easier and faster.
A clear example is Operation PowerOFF: a collaborative effort among law enforcement agencies from 15 countries, coordinated by Europol, to combat the illegal market of DDoS-for-hire services. This operation, concluded in December 2024, led to the seizure of 27 platforms, the arrest of three administrators, and the identification of over 300 clients who used these services to orchestrate attacks.
Despite law enforcement efforts, the DDoS-for-hire market continues to thrive, moving to new platforms and adopting increasingly sophisticated techniques to evade detection.