SSH, or Secure Shell, is an encrypted network protocol used to securely access remote systems. It is commonly used by system administrators and developers to remotely access and manage servers, execute commands and transfer files. While SSH tools are legitimate, they can be exploited for malicious purposes. For instance, cybercriminals have previously distributed malware through a trojanized version of PuTTY, one of the most widely used SSH clients on Windows. In addition, a recent analysis carried out by SANS researchers has shown that threat actors have also abused Windows’ native OpenSSH (suite of secure networking utilities based on the SSH protocol).
In today’s article, we will take a closer look at the behavior of the malware and explore mitigation strategies to prevent it from compromising systems.
Malware Behavior
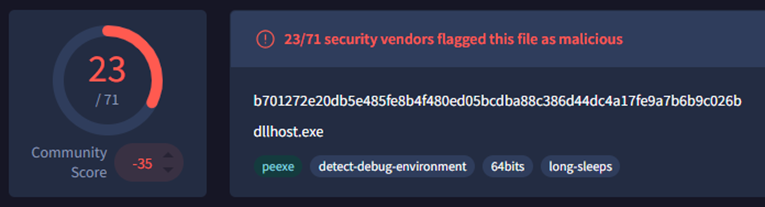
The malicious sample analyzed by SANS researchers can be found on VirusTotal with the filename “dllhost.exe” (SHA256: b701272e20db5e485fe8b4f480ed05bcdba88c386d44dc4a17fe9a7b6b9c026b).
The malware specifically targets the Windows OpenSSH client located at “C:\Windows\System32\OpenSSH\ssh.exe” to implement a backdoor mechanism. Initially, the malware attempts to start an existing "SSHService" service:
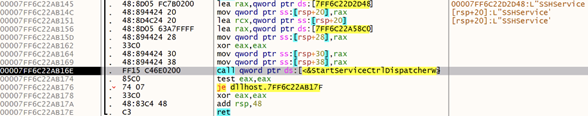
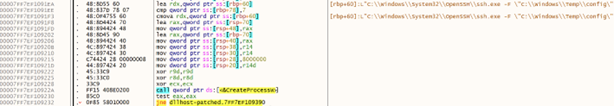
If this attempt fails, it then tries to read the registry key SOFTWARE\SSHservice to access the previously saved random port. In case there is no port saved (first malware execution), a random port is generated and saved. After creating a configuration file that contains the attacker’s Command and Control (C2), the malware enters an infinite loop, performing extended sleep cycles between connection attempts. These cycles aim at avoiding the detection by defensive systems monitoring for rapid, repeated network connections. Each iteration attempts to launch the legitimate ssh.exe process with the malicious configuration file.
Mitigations
This attack technique highlights a growing shift toward the weaponization of legitimate system binaries for malicious purposes. The misuse of OpenSSH is particularly alarming due to its broad presence in Windows environments and its legitimate use for remote connections. To counter such threats, security teams should focus on monitoring unusual configuration files, unexpected network connections to external SSH servers, and registry modifications related to SSH services. In addition, they should also adopt application control measures such as whitelisting to easily distinguish a legitimate service from a malicious one.
Conclusion
This attack reinforces the need for organizations to closely monitor native Windows services, especially the ones with network communication capabilities, as threat actors increasingly exploit the trust in these legitimate system components to bypass security defenses and establish persistence.