One of the most important tools in Digital Forensics is, without a doubt, Volatility.
If you aspire to become an expert in the field (or if you already are), you must become familiar with all the capabilities and functionalities of Volatility.
Volatility is a command-line framework released for free by The Volatility Foundation, which allows forensic analysis of memory dumps, enabling the examination of active connections, running processes, registry keys, and much more.
It can be useful for performing malware analysis on a machine, retrieving information from RAM, and carrying out all activities related to Memory Forensics.
Volatility provides a wide range of features—below we list some of the most relevant ones, but we recommend checking the official documentation for the complete list:
OS INFORMATION
– ImageInfo
vol.py -f "/path/to/file" windows.info
PROCESS INFORMATION:
– PsList, PsScan, PsTree
vol.py -f "/path/to/file" windows.pslist
vol.py -f "/path/to/file" windows.psscan
vol.py -f "/path/to/file" windows.pstree
PROCDUMP
vol.py -f "/path/to/file" -o "/path/to/dir" windows.dumpfiles --pid <PID>
DLLS
vol.py -f "/path/to/file" windows.dlllist --pid <PID>
NETWORK INFORMATION:
– Netscan
vol.py -f "/path/to/file" windows.netscan
vol.py -f "/path/to/file" windows.netstat
FILES:
– Filescan, Filedump
vol.py -f "/path/to/file" windows.filescan
vol.py -f "/path/to/file" -o "/path/to/dir" windows.dumpfiles --(virtaddr/physaddr) <offset>
MALWARE:
– Malfind, Yarascan
vol.py -f "/path/to/file" windows.malfind
vol.py -f "/path/to/file" windows.vadyarascan --yara-rules <string>
Now that we’ve made this necessary introduction, if you’ve opened this article, you’re probably wondering how to dump Windows passwords with Volatility. Let’s proceed without further delay!
To show you a practical example, we need a real use case—a Windows system memory dump to work on. For this, we’ll use the memory dump from OtterCTF, available for download in the Memory Forensics section.
As always, we remind you that before performing memory forensics, malware analysis, or digital forensics in general, it's a good idea to set up a virtual working environment. For that, we refer you to our guide on creating a secure environment (Virtual Machine)!
With that said, we can now begin.
As you might expect, you first need to install Volatility on your device. You can freely download both version 2 and version 3. If you're just starting out with Volatility, we recommend going with the latest version (3.x), so you won’t need to migrate later.
Once the framework is installed and you have a memory image to work with, there are several ways you can proceed to dump Windows passwords.
By searching through the commands listed in the official documentation, we identify one that seems to fit our needs: lsadump.
This command allows you to retrieve sensitive LSA information from the system registry, exposing data such as the default password (if autologin is enabled), the RDP public key, and credentials used by DPAPI.
Running the command on our memory dump gives us a rather interesting output:
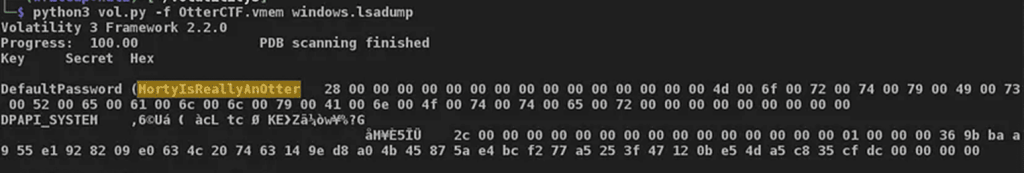
Right in the DefaultPassword field, we find exactly what we were looking for!
An alternative solution to what we’ve shown could be to use the hashdump command, which extracts and decrypts cached domain credentials stored in the registry.
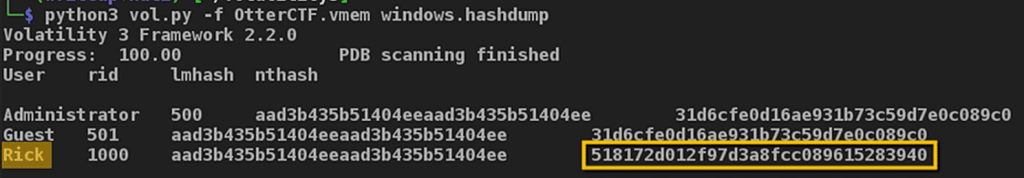
This way, we obtain the password hash of the user accounts present. At this point, we would need to proceed with brute-force to try to retrieve the plaintext password—using, for example, the tool John the Ripper.
We’ve reached the end of this introductory guide on Volatility. If you're interested in diving deeper into cybersecurity topics, we refer you to our other 8-bit guides!