WhatsApp is now an essential tool not only for personal communication but also for business use.
The desktop version of the popular messaging app has transformed a simple chat service into a true ally for companies, facilitating customer management, appointment scheduling, and the distribution of promotional campaigns.
However, this versatility has not gone unnoticed by cybercriminals. The growing popularity of WhatsApp Desktop has made it a prime target for phishing attacks and other cyber threats. One of the most common techniques is impersonation, where an attacker pretends to be an authoritative figure within the company, attempting to deceive employees and obtain sensitive information or privileged access.
But there is an even more serious and often underestimated risk: a vulnerability that allows remote code execution through the WhatsApp Desktop application. This is an attack that requires minimal interaction from the victim, making it extremely dangerous and easy to exploit.
*Disclaimer: This article is written for educational and informational purposes only. The author does not endorse the use of these techniques for illegal or unethical activities. The use of the information contained in this article is at your own risk and responsibility. We encourage you to use these techniques only in authorized testing environments and in compliance with local laws and cybersecurity regulations.*
Context Analysis
At the center of this analysis is one of the most commonly used features on WhatsApp: file sending. In the Desktop version, when a user receives a file, there are two main options: “Open” and “Save.”
For convenience, many tend to choose the “Open” option, avoiding the longer and seemingly unnecessary save procedure. But this apparently harmless behavior raises an important security question: what happens if a malicious file is sent, such as an executable (.exe)? Is it possible to disguise it in a way that induces the victim to click on “Open”?
Driven by this curiosity, we conducted some tests to understand the actual vulnerabilities of the platform. From our first attempts, we can see that it’s not actually that simple:
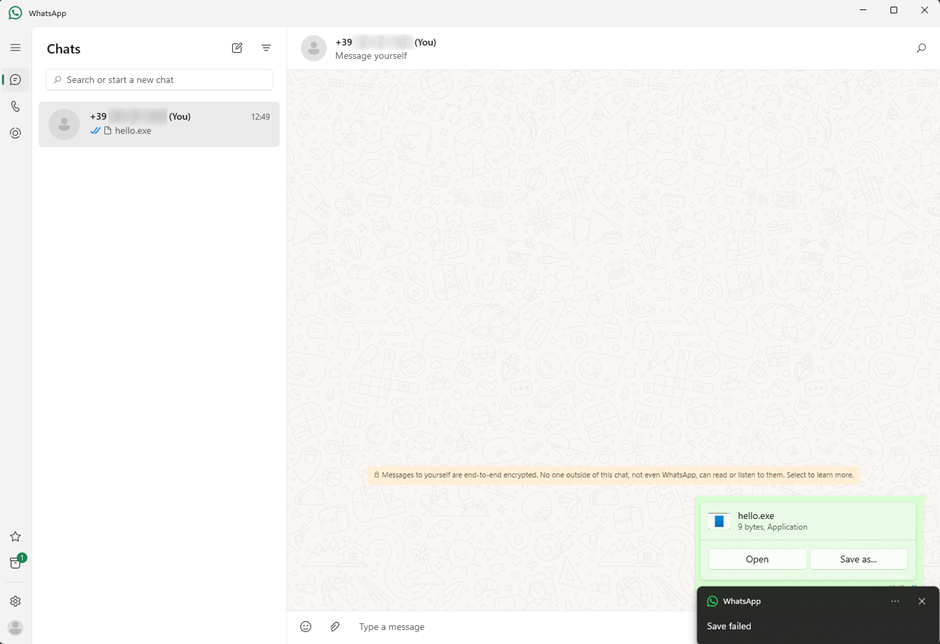
Apparently, there is a small security mechanism in WhatsApp that prevents direct launching of applications. Therefore, the victim would need to first save the file with a specific name and then manually launch it, which definitely requires a certain level of interaction and could more likely trigger the antivirus or EDR.
It’s clear that this solution is not viable. But we decide not to give up and try with “.vbs” and “.hta” file types as well: these attempts are also unsuccessful.

Exploiting the Vulnerability
But what happens if, instead, we send a compressed Python file, in the “.pywz” format?
To find out, we simply experiment: we write a small code snippet that opens the calculator and see if anything changes:
import subprocessdef avvia_calcolatrice():try:subprocess.run("calc.exe", check=True)except Exception as e:print(f"An error occurred: {e}")if __name__ == "__main__":avvia_calcolatrice()
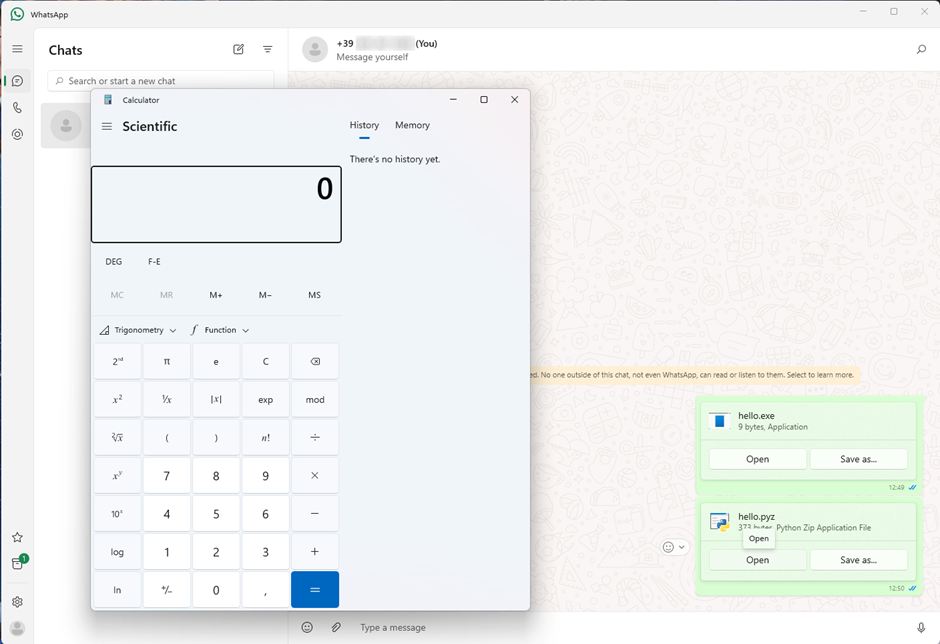
Bingo! WhatsApp executes the code contained in the Python file without any kind of problem or warning alert.
Having achieved this, it’s easy to imagine how, with a simple Python script, one could execute any action on the machine with the current user's privileges. For example, one could open a reverse shell on the victim's device.
At this point, advanced obfuscation techniques cannot really be applied. However, we can take advantage of WhatsApp’s character limitation for displaying file names to hide the suspicious extension and try to deceive our victim:
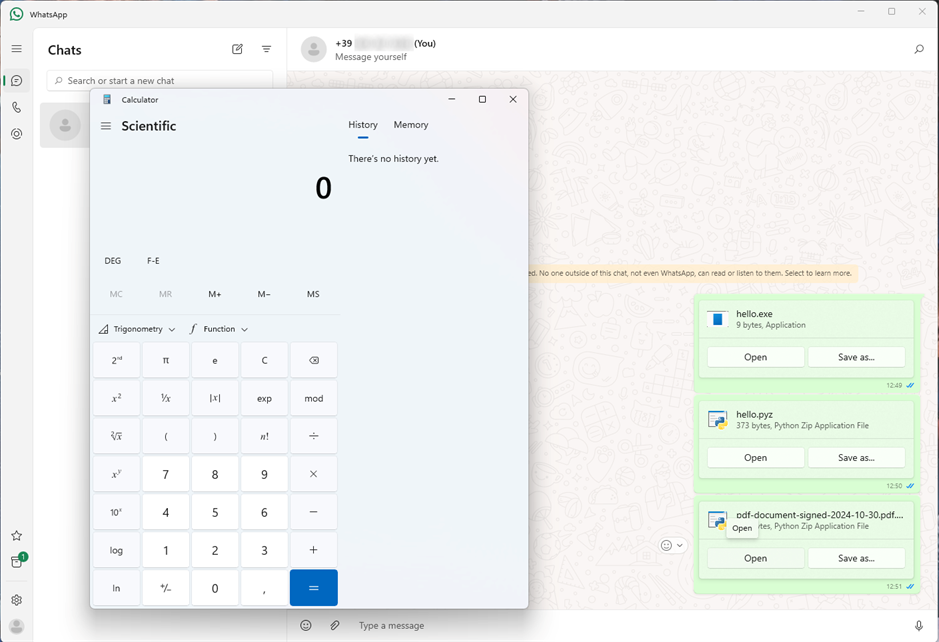
Et voilà! Surely it won't be easy to fool the most attentive users, but how hard would it be to find someone who doesn’t recognize the Python icon and might absentmindedly read the “.pdf” extension?
What’s extremely interesting is that the code is executed instantly, without any prompt window that might arouse suspicion and without any warning screen. A single careless click, and it’s already too late.
What Does the Meta Team Say About This?
Digging deeper, we discover that the issue is already known and was reported by a researcher, Saumyajeet Das, in June 2024:
“I have reported this issue to Meta through their bug bounty program, but unfortunately, they closed it as N/A. It’s disappointing, as this is a straightforward flaw that could be easily mitigated,” – he stated in an interview with BleepingComputer.
The tests we carried out at 8Bit Security refer to version 2.2445.7.0, currently the most recent available.
In his publication, Saumyajeet Das highlights how the same flaw can also be exploited with PHP files.
From other tests we conducted, we also found that even “.ps1” files are not blocked. The “fortunate” part here is that the OS opens this type of file with Notepad and does not directly execute the script.
It’s clear that Meta is not giving this vulnerability the attention it deserves, despite the evident risk that it could be easily exploited by malicious actors. A flaw like this could cause significant damage, both personally and at the company level.
The hope is that increased awareness will prompt Meta to take prompt action, implementing the necessary countermeasures. Among these, it would be advisable to block the sharing of “anomalous” or potentially dangerous file extensions and to introduce explicit warnings for users attempting to open or save suspicious files