An Increasing Number of Emerging Tools Are Entering the Market for OSINT Activities in Cybersecurity
More and more emerging tools continue to enter the market for OSINT activities in cybersecurity. It's not always easy to understand which ones to rely on, in what context they may be useful, and how to get the most out of them.
For this reason, we’ve put together a list of 10 tools selected by the 8BitSecurity editorial team, which we believe should be essential instruments for every good cybersecurity analyst.
Before diving into the presentation of each tool, let’s briefly introduce the concepts of OSINT and IOCs.
If you prefer to skip directly to the list, here is a navigation index for the article:
- VirusTotal
- AbuseIPDB
- Shodan
- AlienVault
- Tirexdel
- MalwareBazaar
- Cisco Talos Intelligence
- IBM XForce
- Censys
- Kaspersky TIP
What is OSINT?
Before figuring out which tools are best suited to your needs, it might be useful to start with a quick introduction to the topic. OSINT stands for “Open Source Intelligence,” a practice of collecting and analyzing information from a wide range of public and open sources such as websites, social media, online forums, news articles, and more, with the goal of gaining a deeper understanding of specific topics, individuals, organizations, or events.
This discipline has a wide range of applications:
- Vulnerability research
- Brand protection and phishing detection
- Threat and imminent attack monitoring
- APT and threat actor analysis
- Supply chain monitoring
- Malware and Command and Control (C2) activity analysis
- Analysis of IOCs (Indicators of Compromise)
How Can OSINT Analysis Be Applied in a SOC Context?
First and foremost, you can certainly enrich your knowledge of indicators of compromise, allowing you to generate, identify, and most importantly, analyze potential security incidents that impact your organization's perimeter.
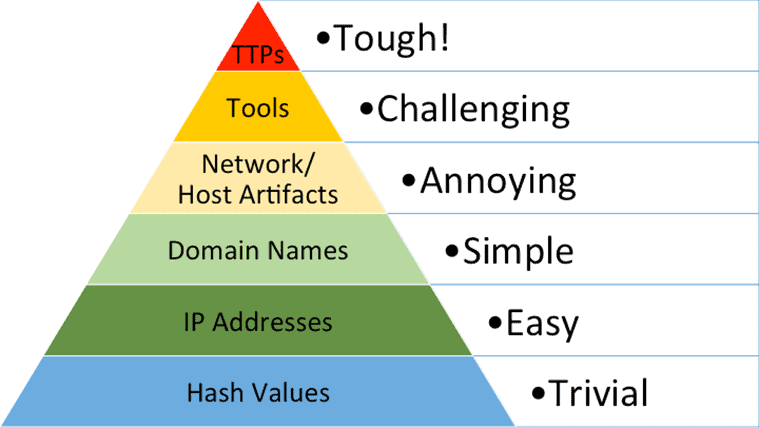
An Indicator of Compromise (IoC) is a host or network artifact that potentially indicates an ongoing attack or a compromise that has already occurred against an IT system. Sharing IoCs is fundamental to preventing similar threats, and for this reason, “sharing communities” based on this concept are becoming increasingly frequent and important.
IoCs can take various forms, and their collection may be more or less complex depending on the level at which they operate, as conceptually described by David Bianco’s Pyramid of Pain:
The 10 Best Tools Selected by the Editorial Team
Here we are with the list of the 10 OSINT tools selected by the editorial team of 8Bit Security. The list below is not a ranking nor an exclusive list: the platforms we decided to present were chosen based on our experience, with the goal of not only introducing you to essential tools for your daily work as a security analyst but also providing you with a diverse set of tools with different focuses and features.
VirusTotal
In an article like this, it’s impossible not to start with VirusTotal, which we imagine needs no introduction.
In case it does, it is a web platform founded in 2004 as a service for analyzing files and URLs for viruses, worms, trojans, and other types of malicious content.
Over the years, it has added support for more than 80 antivirus engines, including major vendors like Kaspersky, CrowdStrike, BitDefender, ESET, and MalwareBytes. Now owned by Google, it is one of the leading reference databases for searching malicious and non-malicious file hashes, domains, URLs, and IP addresses.
Key features include:
Scanning files from your device using automatic sandboxes.

Figure 2. File uploading to VirusTotal Searching artifacts in its proprietary database, such as IP addresses, domains, URLs, and file hashes.
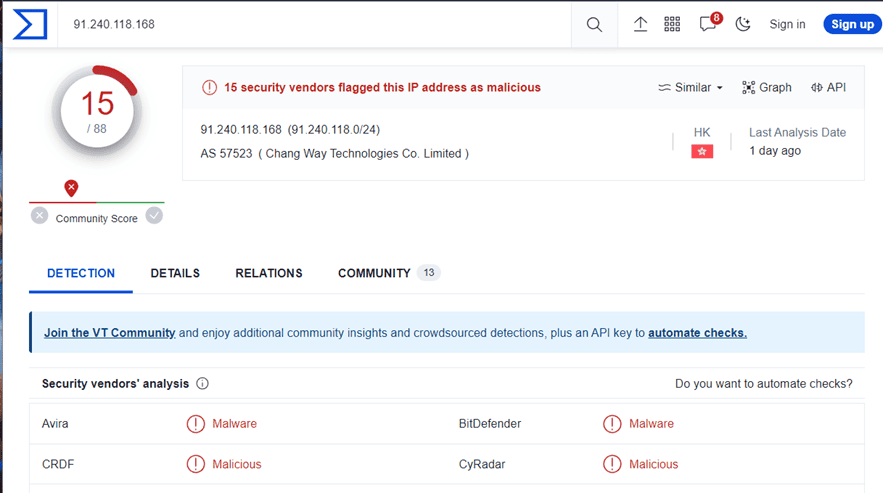
Figure 3. IP address analysis on VirusTotal
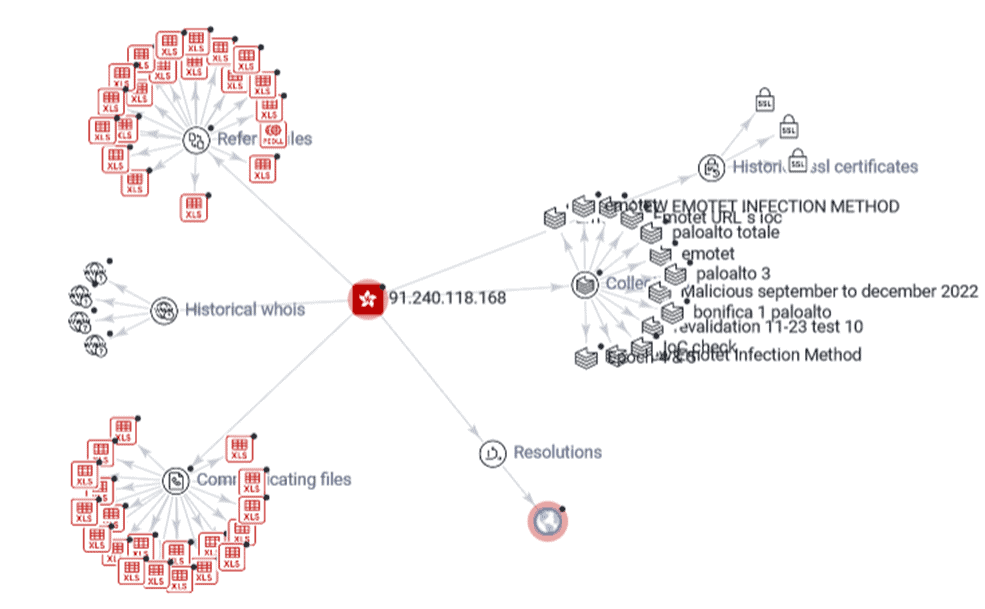
After querying an indicator, a detailed report is returned, navigable through various menu items, including: deeper information in the Details tab (such as WhoIs and HTTPS certificate for IP addresses or string and metadata analysis for files); links to other indicators in the Relations tab; and the opinion of the Community, i.e., registered users.
Finally, via the Graph button, you can access a graphical view of the indicator’s relationships, as already shown in the Relations tab.
VirusTotal also offers several additional services, some via subscription, such as APIs for automated analysis, threat hunting support modules, and the ability to search and apply Yara Rules to files in its database.
Use Cases:
VirusTotal is a very complete and versatile tool. You’ll find yourself using it in almost every situation: from analyzing indicators of compromise (IoCs) discovered during an incident, to investigating suspicious files, or evaluating IoCs to be blocked on perimeter systems.
Its strong point is the analysis of malware-related activity.
AbuseIPDB
AbuseIPDB is a project developed by Marathon Studios Inc. that acts as a reference database for IP addresses associated with malicious behavior on the Internet.
It is heavily community-driven, allowing users to report suspicious IPs or those involved in malicious activities such as cyberattacks, brute-forcing, scanning, spam, and phishing attempts.
The service provides a reputation score for each IP address, which helps users assess its associated risk level.
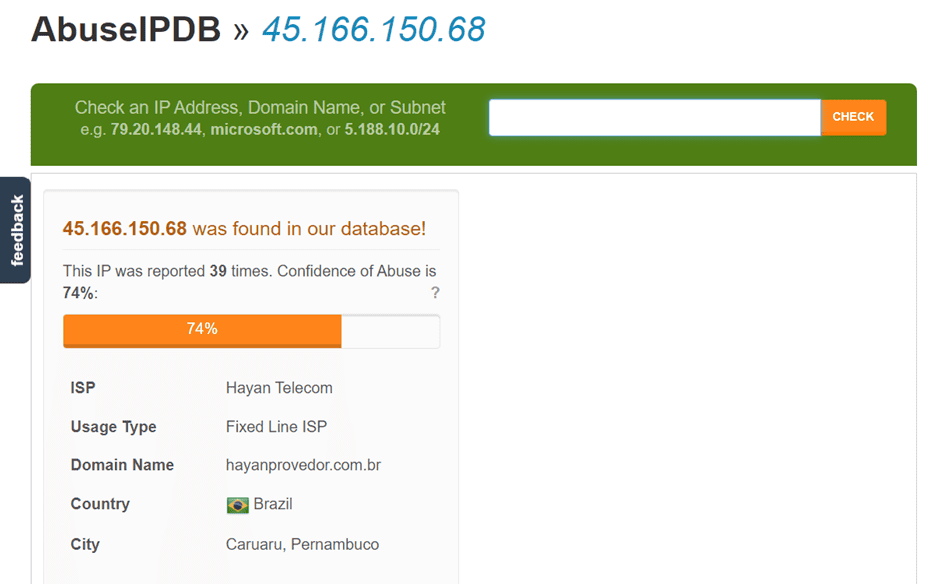
Because the score is not based on a structured analysis process but rather on community opinions, it is inevitably subject to inaccurate or low-quality reports, which sometimes casts doubt on the tool’s reliability.
Despite this, it remains one of the most used services by professionals in the field for IP address analysis in incident management activities.
Use Cases:
Weighing the pros and cons of this portal, we can say that AbuseIPDB deserves a spot among your “must-have tools” as a security analyst.
Its ideal use case is in analyzing and identifying IP addresses known for scanning, brute-forcing, WAPT, and similar behaviors.
Shodan
Shodan is a specialized search engine designed to find devices and services connected to the Internet. Unlike traditional search engines like Google, which primarily index web pages and online content, Shodan focuses on indexing devices and services, providing detailed information about them.
Shodan primarily offers the following features:
Scanning exposed devices on the Internet: It performs worldwide scans to find devices like surveillance cameras, servers, routers, IoT devices, industrial control systems, and more.
Collecting detailed information: Once devices are found, Shodan gathers detailed data such as the operating system in use, open ports, active services, SSL certificates, and other technical details.
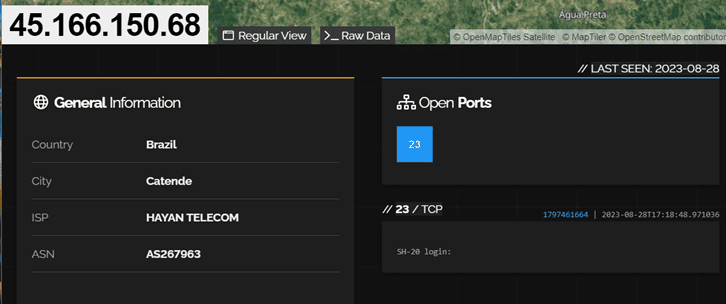
Figure 7. IP address report on Shodan Advanced search: Shodan offers a powerful search capability that lets users find specific devices or services based on criteria such as device type, geographic location, manufacturer, known vulnerabilities, and more.

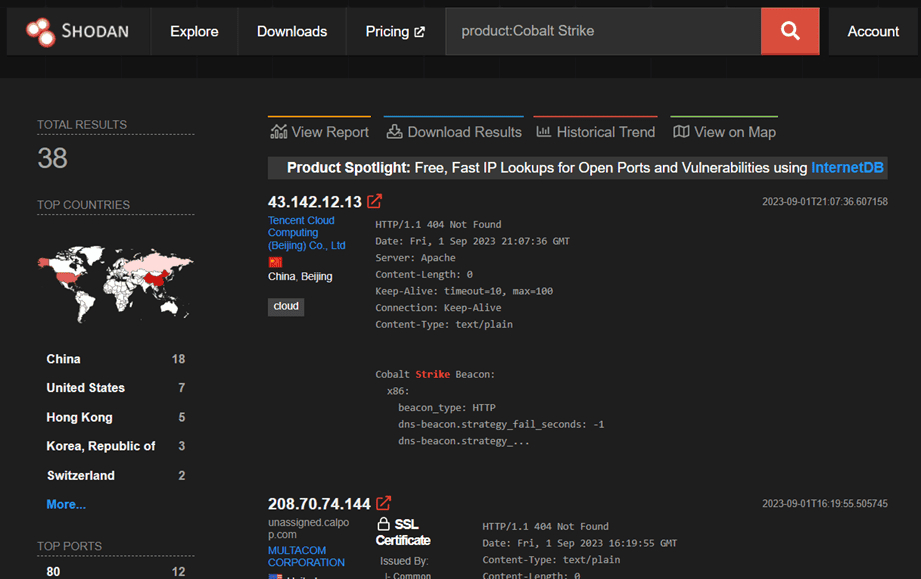
Figure 8. Query example for Cobalt Strike C2 on Shodan Monitoring public information: The data collected by Shodan is public and accessible to anyone. Network administrators and cybersecurity professionals can use the service to identify exposed and potentially vulnerable systems.
While Shodan was created to help cybersecurity experts improve their organization’s security posture by identifying vulnerable devices, it can also be misused by malicious actors to study vulnerable devices as potential attack targets.
Use Cases:
Shodan is another very versatile tool, though it provides different types of data compared to the previous platforms discussed.
Its great usefulness shines in proactive threat research, also known as Proactive Surveillance feeds. Through its search engine, you can identify exposed assets within your organization that do not comply with security policies, and perform targeted queries to preemptively identify C2 infrastructures used by malicious actors.
AlienVault OTX
AlienVault OTX, short for “Open Threat Exchange,” is a real-time threat and attack information sharing platform for cybersecurity professionals and interested organizations.
This tool allows users to access data and Indicators of Compromise (IOCs) collected by a vast global community of security users and researchers. Users themselves can contribute by reporting and sharing information about malware, vulnerabilities, suspicious IP addresses, and more. These are then made available to all OTX users to improve their understanding of cyber threats and strengthen their security posture.
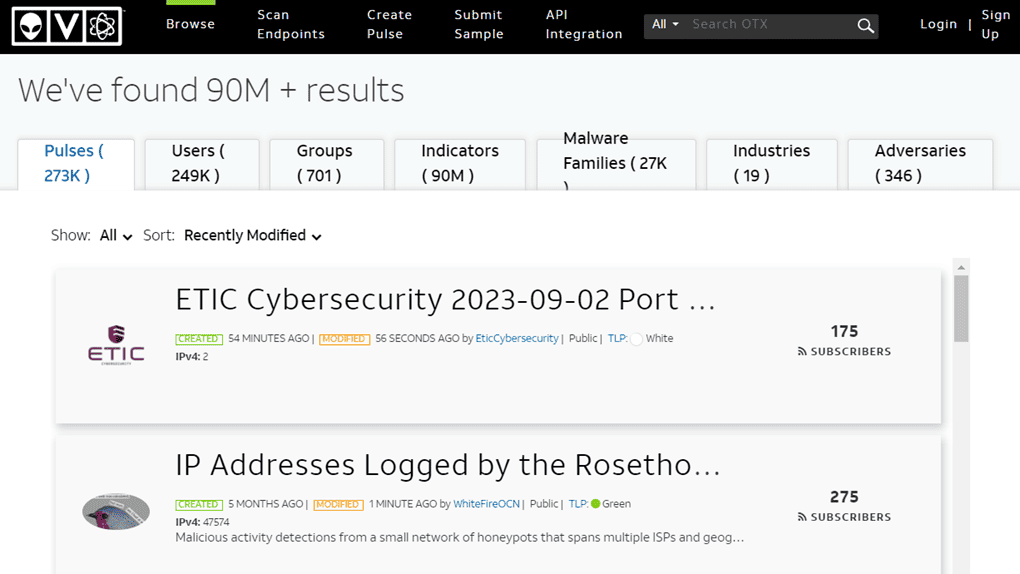
The platform offers an intuitive interface for searching, analyzing, and downloading compromise and attack indicators. The data can be used by companies, government organizations, and cybersecurity professionals to enhance threat detection and response, protect their systems and networks, and share relevant security information with the global cybersecurity community.
Each user can create a “Pulse,” which is a collection of host or network artifacts identified as malicious, and make it available to the community:
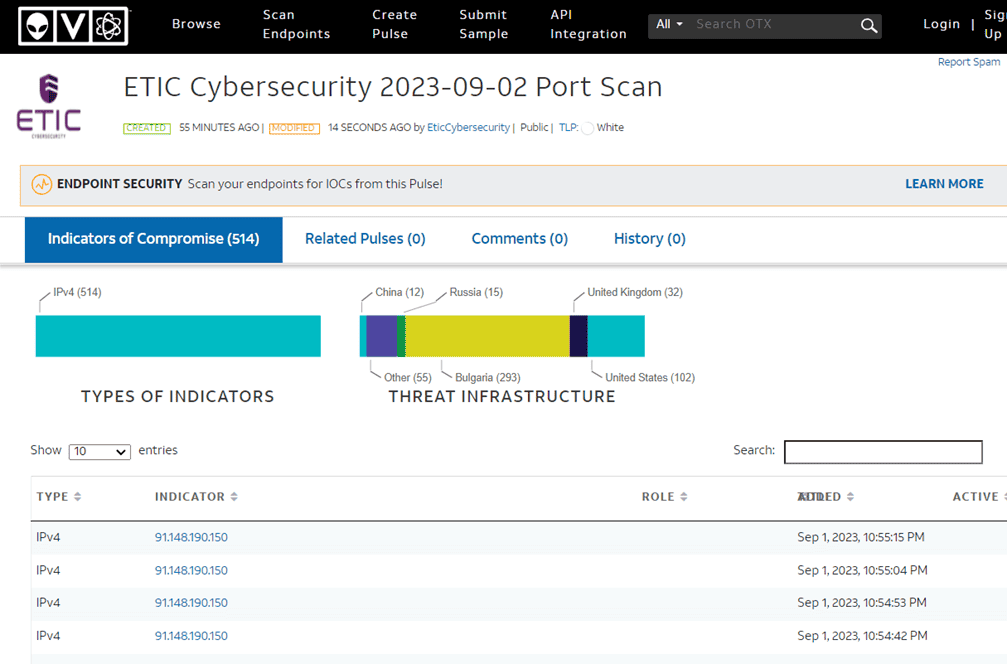
Finally, it is also possible to conduct specific searches for compromise indicators via the database provided by AlienVault.
In the example below, we show the search for an IP address on the portal:
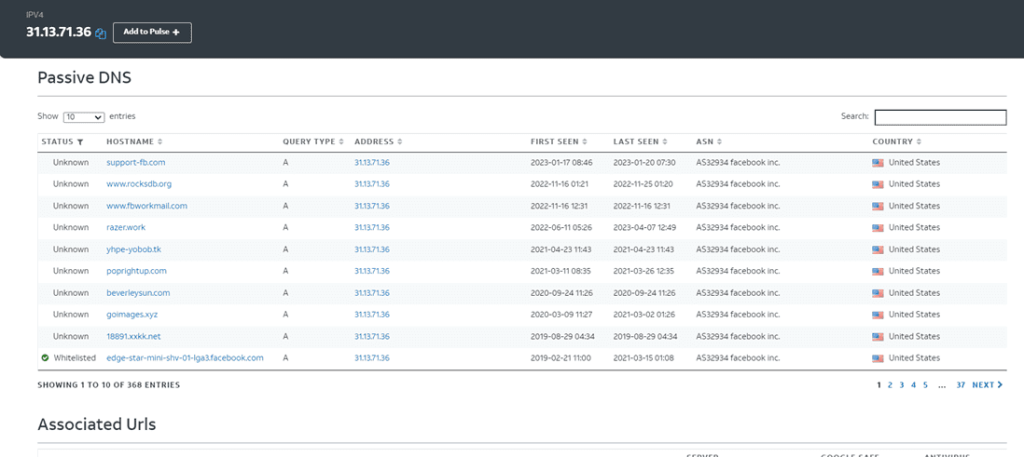
Among the most interesting information the portal offers, you can find a list of all domains and URLs associated with IP addresses.
Use Cases:
In this guide, AlienVault clearly takes the lead when it comes to Cyber Threat Intelligence activities. In addition to the database for IOC searches, the platform enables its community to exchange feeds on the most recent attacks and related IOCs.
In a practical analysis use case, it can be very helpful in studying suspicious IP addresses. AlienVault provides all passive DNS entries associated with an address over the past years, making it possible to distinguish false positives and unreliable indicators.
Tirexdel
Wouldn't it be great to have all the information from the portals we've seen so far—and more—presented on a single platform with a single search? If that sounds good to you, know that it exists!
Tirexdel is an OSINT tool available as a Windows executable that allows you to streamline operations by autonomously searching and processing all the information you need during the analysis phase of one (or many!) compromise indicators and artifacts.
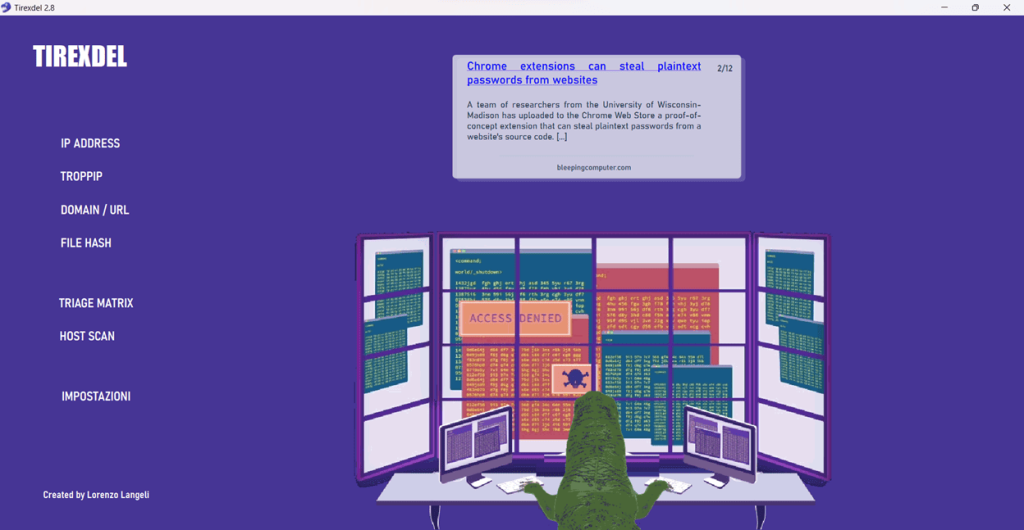
The interface is quite intuitive: by navigating the left-side menu, you can scan IP addresses, domains, URLs, and file hashes.
At the top right, you’ll find a news ticker showing the day’s most relevant cybersecurity news.
In the example below, we show a query for several IP addresses:
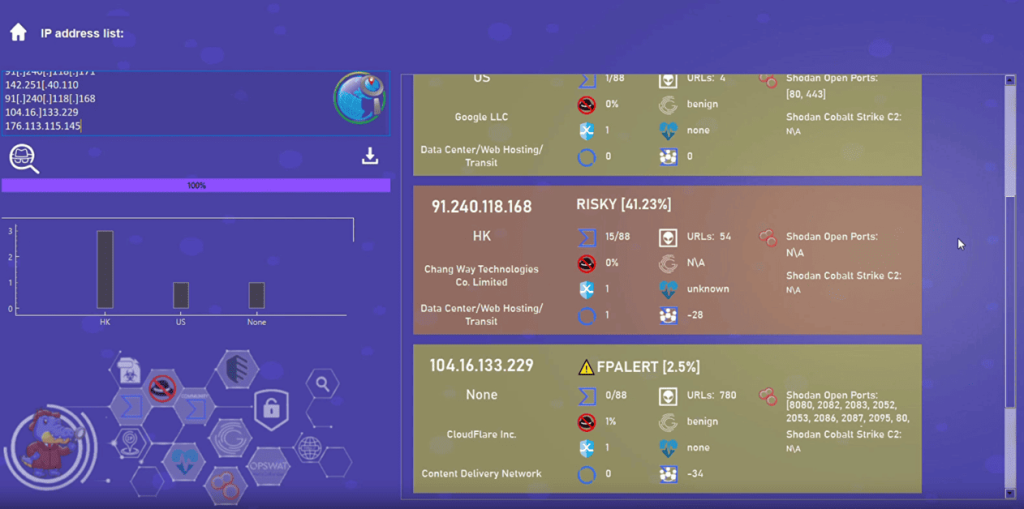
The script’s output can also be downloaded via a dedicated button, producing a processed report with all the useful information.
Currently, Tirexdel supports a total of 9 different vendors, including VirusTotal, AbuseIPDB, AlienVault, Shodan, and others.
Tirexdel can be downloaded for free from its dedicated GitHub page, where you’ll also find a more detailed description of all its features.
Use Cases:
Tirexdel brings together all major security vendors for OSINT and threat intelligence analysis in a single tool. Its usefulness in a SOC environment allows a security analyst to streamline and automate processes during incident handling and in the verification and analysis of possible Indicators of Compromise.
MalwareBazaar
MalwareBazaar is an online project that functions as a malware repository and analysis platform.
It was created to allow cybersecurity experts, researchers, and analysts to share, analyze, and access malware samples from around the world. This resource is used to study cyber threats, identify new malware types, analyze infection techniques, and develop cybersecurity countermeasures.
MalwareBazaar users can upload real malware samples, including executables, scripts, infected documents, and more, thus contributing to community knowledge of specific threats. The platform provides analysis tools to examine samples, detect suspicious behavior, and generate Indicators of Compromise (IOCs) useful for threat detection and mitigation.
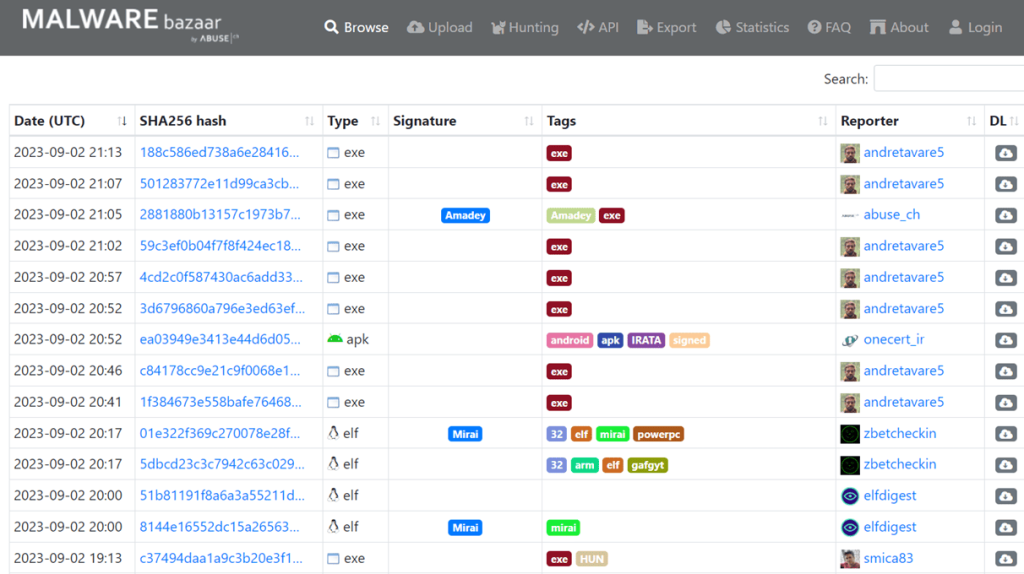
With the appropriate filters, you can perform ad hoc queries to search for specific malware by name, tags (such as family), and hash.
Samples can then be downloaded for deeper analysis.
Among its other features, the platform also includes a statistics page for malware trends and a hunting module that lets users receive alerts based on defined parameters; for example, you can set an alert for every new Trickbot sample.
Use Cases:
Primarily useful for researchers in the field of Malware Analysis, MalwareBazaar can support incident analysis by helping to search for specific malware or gather new Indicators of Compromise.
Cisco Talos Intelligence
Cisco Talos Intelligence is a division of Cisco Systems, one of the leading companies in the IT industry.
Talos Intelligence focuses on cybersecurity and operates as an advanced research group specializing in identifying and analyzing cyber threats.
The Cisco team conducts all major intelligence activities, including threat research, malware analysis, and the detection and sharing of new IOCs.
Specifically, the platform is designed and structured with a primary focus on global email traffic.
Using the dedicated search bar, users can query specific IP addresses, subnets, domains, and network owners to obtain contextual information, a reputation score, and statistics on email traffic generated over a recent period.
In the example below, we show an IP address query on the platform:
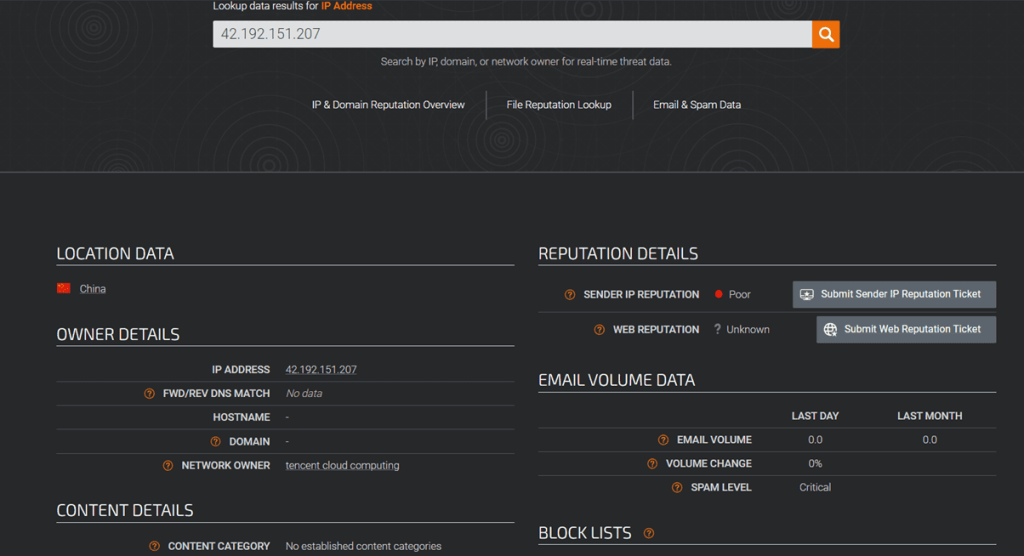
The information displayed includes geolocation of the asset, ownership details, reputation score, volume of generated email traffic, and whether it appears on public blocklists.
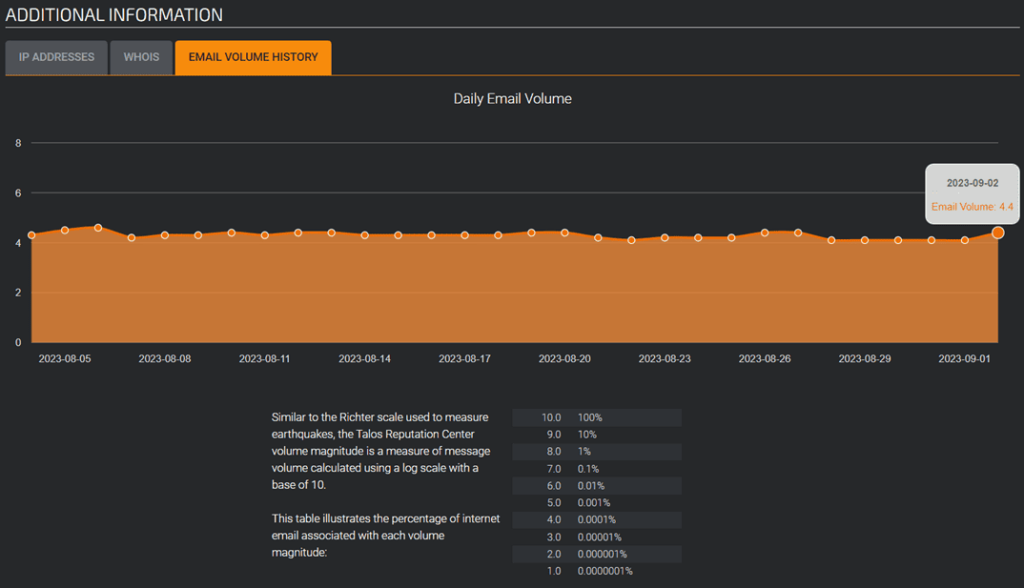
Finally, under “Additional information,” selecting “Email volume history” lets users view historical statistics on generated traffic.
Use Cases:
As mentioned, the data collected by Cisco Talos Intelligence is highly targeted toward the world of email traffic. The best use case is in the analysis of phishing emails: through the reputation score and traffic statistics for SMTP/IMAP/POP3 generated by an IP and its subnet, you can distinguish potentially malicious IP addresses from those of major internet service providers.
IBM X-Force
IBM X-Force is a cybersecurity organization managed by IBM, one of the world’s leading technology and IT services companies. X-Force specializes in identifying, analyzing, and defending against cyber threats and plays a critical role in protecting networks, systems, and data for organizations worldwide.
It is another Threat Exchange portal, but unlike AlienVault, the information shared is primarily provided directly by the vendor rather than a broader user community.
Through its dashboards, users can access intelligence on emerging threats, new malware, detailed reports on APTs and threat actors, and more.
One of its most useful features is the ability to search the database for all types of artifacts and indicators, much like VirusTotal and AlienVault.
In the example below, we show an IP address search on the platform:
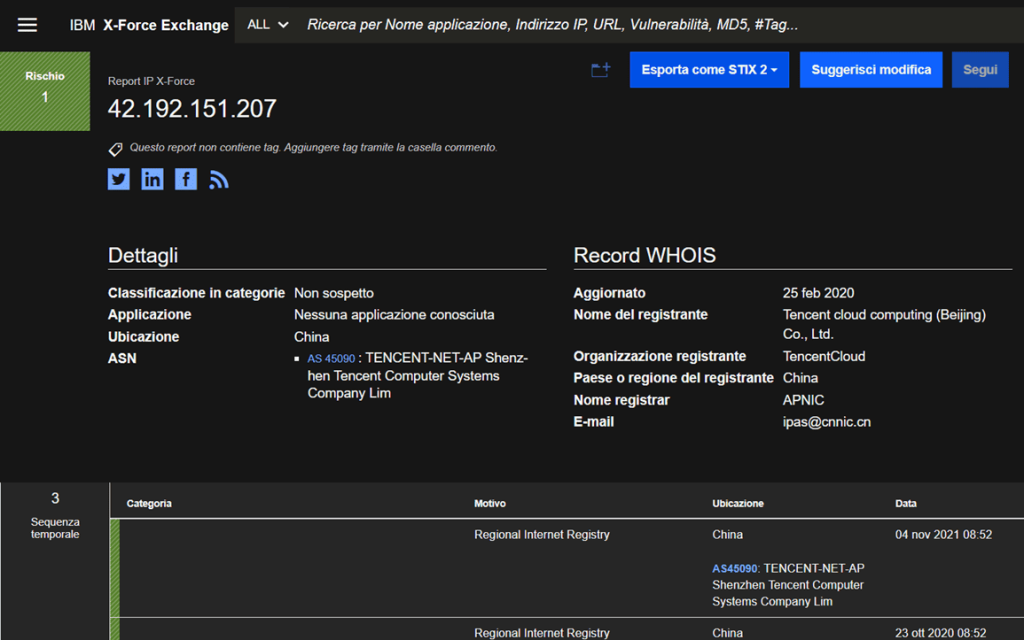
IBM is considered one of the top-tier vendors in the field, and the data it shares and provides is undoubtedly among the most valuable when analyzing incidents.
Use Cases:
IBM X-Force has a wide range of applications. As a security analyst or researcher, it can be an important asset during the investigation of an Indicator of Compromise linked to an incident.
Censys
Censys is a digital platform that provides internet-wide scanning and monitoring of digital assets. It is mainly used by cybersecurity professionals and organizations to identify, analyze, and manage digital assets—including servers, IoT devices, and online services—to improve cybersecurity and ensure compliance with security policies.
Censys performs automated internet scans to identify and collect detailed information about these assets, such as IP addresses, open ports, SSL/TLS certificates, software versions, and more. The collected information is made available through an intuitive user interface, allowing users to monitor attack surfaces, detect vulnerabilities, protect sensitive data, and identify suspicious activity.

As you may have guessed, this service is quite similar in nature to Shodan.
Indeed, the search methodology is very similar, and the output is often comparable.
In the example below, we show a query for an IP address on the platform:
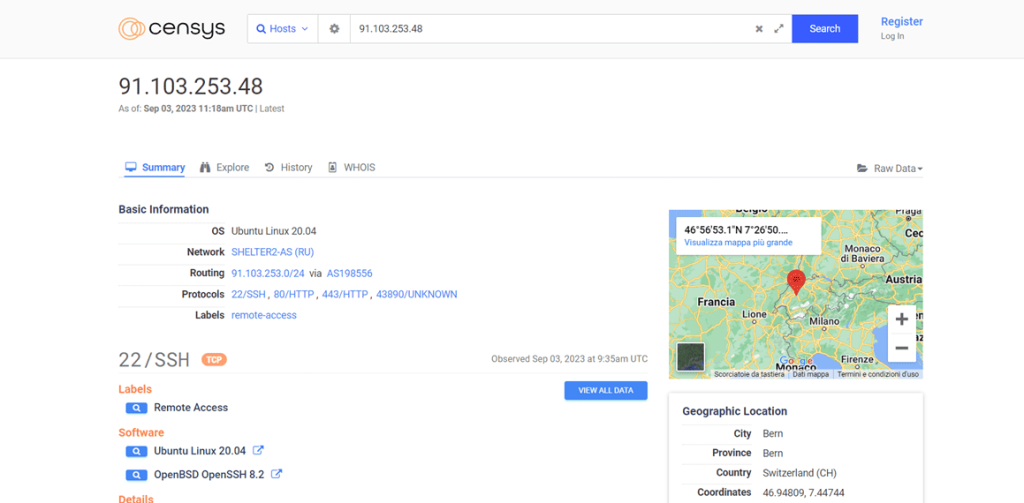
The service provides various data such as the host’s WhoIs, OS fingerprint, open ports, and exposed services. It also allows users to track historical data to observe its evolution over months or years.

In summary, Censys is an essential tool for gaining visibility into an organization’s digital presence on the internet. It helps identify potential risks and improve cybersecurity. It is used to evaluate, protect, and effectively manage an organization’s online assets.
Use Cases:
Its use cases are nearly identical to those of Shodan.
Its strength lies in proactive threat discovery, also known as Proactive Surveillance feeds. Using its search engine, you can identify exposed assets in your organization that do not comply with security policies, or run targeted queries to detect the C2 infrastructures of malicious actors.
Kaspersky Threat Intelligence Portal
The Kaspersky Threat Intelligence Portal is a service offered by Kaspersky, a multinational cybersecurity company headquartered in Russia. This portal is designed to provide real-time information and resources about cyber threats and help organizations understand them more effectively.
Through the Threat Intelligence Portal, users can access updated data on malware, cyberattacks, vulnerabilities, and other emerging threats. This information is useful for cybersecurity analysts, network administrators, and experts seeking to protect their systems and data from potential attacks and intrusions.
The portal also provides data on threat trends and ongoing attack campaigns, keeping users informed about the latest developments in cybersecurity. This intelligence can help improve defense strategies, detect threats more promptly, and adopt preventive measures.
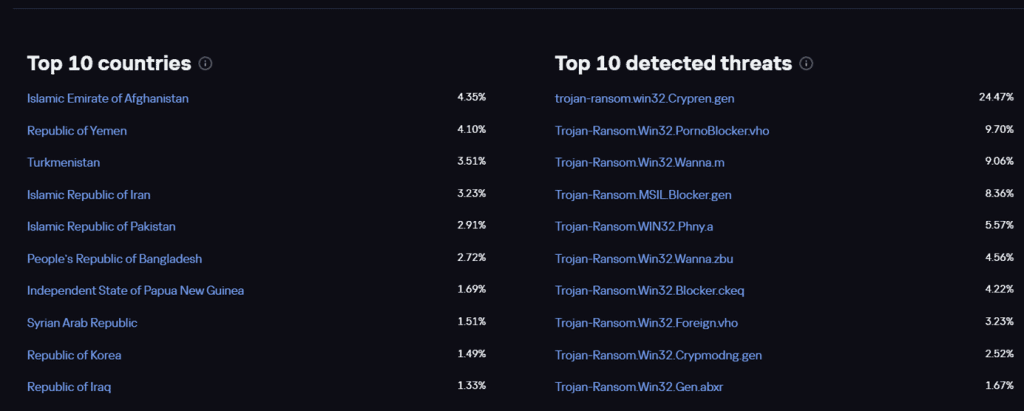
Only some features are freely available.
Among them, Kaspersky allows users—similar to VirusTotal—to run automated scans on files from their local machines.
In the example below, we show the analysis of a Windows/System32 file from our own device:
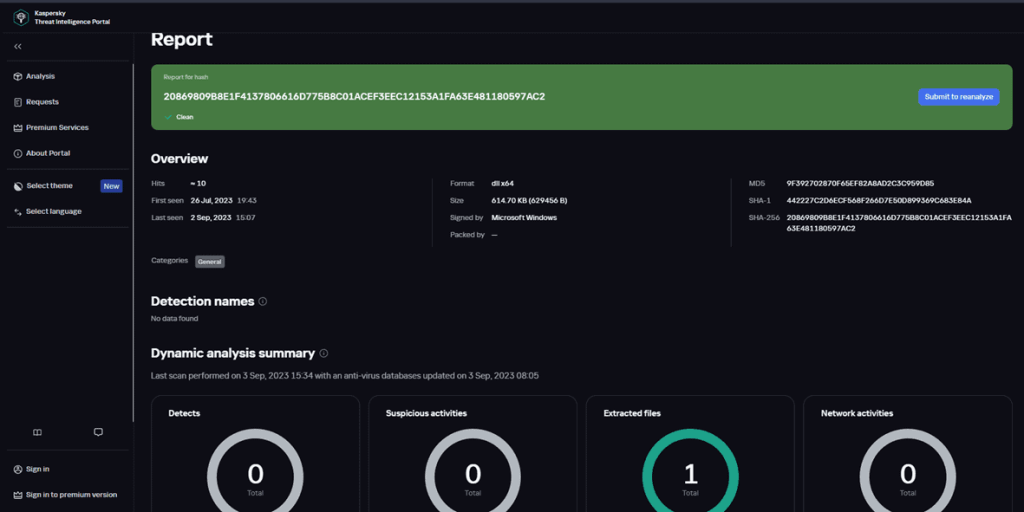
Finally, like other platforms covered in this article, Kaspersky also lets users search for indicators in its database and view information known to the vendor.
In the example below, we show an IP address query on the portal:
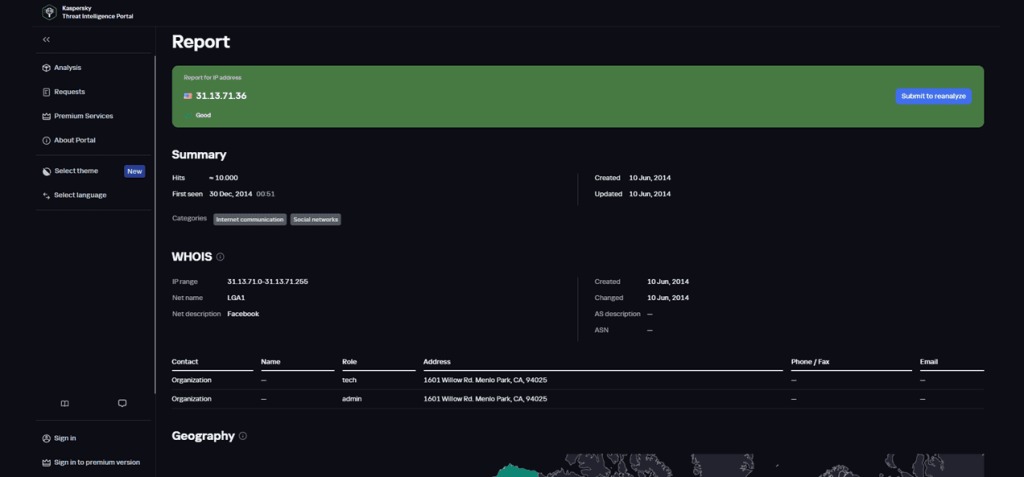
Use Cases:
Thanks to its antivirus engine, Kaspersky TIP is particularly useful in malware analysis. Its “Lookup” functionality is also valuable when analyzing Indicators of Compromise following a security incident.
And that's it for today! Hope you like this article. In case, keep following us!